Introduction
Zero Trust Architecture (ZTA) is a strategic cyber security version that operates at the precept in no manner trust, continuously verify. Unlike traditional safety tactics that count on the entirety indoors a network perimeter is inherently sincere, ZTA recognizes that threats can originate from each outside and inside the network. It removes implicit be given as authentic with and rather needs strict identification verification for everyone, device, and application attempting to access assets, irrespective of their region.
The center guideline of Zero Trust is that no entity, whether or now not human or system, need to be granted automatic resources on its community region. Every get entry to request is treated as though it originates from an untrusted community, and non-stop verification is performed earlier than granting and preserving. This model appreciably reduces the assault surface and minimizes the capability impact of a protection breach by stopping lateral movement inside the network. At its heart, ZTA is built upon three foundational ideas: Verify Explicitly: Every get entry to request may be very well authenticated and licensed all available records elements. This includes customer identification, tool posture (fitness, compliance, protection updates), region, the service or workload being accessed, and the category of the data. Enforce Least Privilege Access: Users and gadgets are granted great the minimal essential to perform their authorized functions. This idea, called "simply-in-time" (JIT) and really-enough (JEA), limits functionality exposure or damage from compromised bills or insider threats. Assume Breach: ZTA operates below the notion that breaches are inevitable. Therefore, the structure is designed to reduce the "blast radius" if a breach happens. This consists of micro-segmentation of sensitive assets, give up-to-stop encryption, non-stop tracking of customer and tool behavior for anomalies, and robust incident reaction and healing mechanisms.
Benefits & Use Cases
Zero Trust Architecture offers a large number for cutting-edge businesses going through an increasingly complicated chance panorama:
Benefits:
Enhanced Security: By putting off implicit recall and enforcing non-prevent verification, ZTA considerably reduces the attack floor. It offers strong safety towards each outside and insider threats, making it notably harder for unauthorized users to benefit for malware to unfold. Reduced Attack Surface: Micro-segmentation, a key factor of ZTA, divides the network into smaller, isolated segments. This limits lateral movement for attackers, containing breaches to a smaller region and stopping them from accomplishing essential property. Improved Data Protection: ZTA ensures that touchy records is protected at every layer via the usage of imposing strict controls and regularly requiring end-to-quit encryption. This permits agencies comply with facts privateer’s recommendations like GDPR and HIPAA. Adaptability to Dynamic Environments: In today's hybrid and multi-cloud environments, traditional perimeter protection is inadequate. ZTA offers a constant safety model across on-premises, cloud, and a ways off paintings settings, providing flexibility and scalability. Strengthened Remote Work Security: With the rise of remote and hybrid workforces, ZTA is vital for securing corporation assets from any place and tool, treating a ways off endpoints with the same scrutiny as on-website online connections. Better Visibility and Control: ZTA offers granular visibility into community sports activities, permitting protection organizations to show who's accessing what property, from in which, and at what time. This heightened visibility aids in detecting unusual behavior and responding brief to incidents.
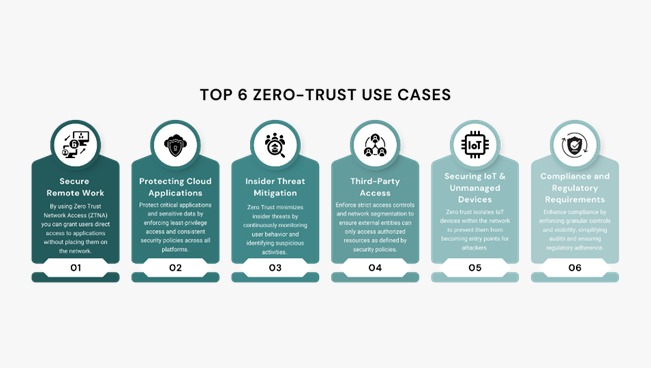
Use Cases:
Securing Remote and Hybrid Work Environments: ZTA is good for offering strong applications and records for personnel walking from numerous locations and the usage of various devices, often changing or augmenting traditional VPNs. Protecting Cloud Deployments: As companies more and more adopt IaaS, PaaS, and SaaS, ZTA gives a uniform protection model for the duration of one of a type cloud systems, ensuring everyday protection for workloads and facts in the cloud. Controlling Third-Party and Partner Access: ZTA allows companies to supply as a substitute granular, least-privilege external contractors, corporations, and companions, without exposing the complete network or requiring endpoint marketers. Mitigating Insider Threats: By constantly verifying consumer identity and tool posture, and implementing least privilege, ZTA notably reduces the chance of unauthorized and lateral movement by means of malicious or compromised internal clients. Safeguarding IoT and OT Devices: Extending Zero Trust principles to business manipulate systems (OT) and Internet of Things (IoT) devices allows guard them through imposing least-privileged policy controls and tracking their behavior.
Conclusion
Zero Trust Architecture (ZTA) is no longer an optional security model—it has become a necessity in today’s rapidly evolving digital landscape. By eliminating implicit trust, enforcing continuous verification, and applying least-privilege access, organizations can significantly strengthen their defenses against both external and insider threats. From securing cloud workloads and remote workforces to protecting IoT and critical infrastructure, ZTA provides a flexible, scalable, and future-ready approach to cybersecurity.
At TeacherCool, we believe in equipping learners and professionals with the knowledge and tools to adapt to these cutting-edge cybersecurity practices. By understanding and implementing Zero Trust principles, individuals and organizations can stay ahead of threats, safeguard sensitive data, and build a more resilient digital future.